Wednesday, July 29, 2020
Tuesday, July 28, 2020
Wednesday, November 27, 2019
How to take consistent backups at standby site
How to take an offline, consistent, self-contained backup at the standby site. The aim of this exercise is to have a self-contained backup that can be restored on its own without needing recovery. I.e., since recovery of standby is stopped, the backup is a cold backup.
1) stop managed recovery:
2) backup the database and controlfile
Please note :- If you have a recovery catalog configured you can connect to it and take a backup.
Both the Primary and Standby database should use the same recovery catalog. Even though these database share the same DBID,Rman is able to differentiate the standby database from Primary .
Note you do not need to register the standby database in the catalog if the primary is already registered. Simply connect to the standby as target and then connect to recovery catalog for taking backup.
RMAN> backup database plus archivelog ;
RMAN> backup current controlfile;
The above will result in a consistent, self-contained backup.
3) restart managed recovery:
To restore from this backup:
1) stop managed recovery:
SQL> ALTER DATABASE RECOVER MANAGED STANDBY DATABASE CANCEL;
2) backup the database and controlfile
Please note :- If you have a recovery catalog configured you can connect to it and take a backup.
Both the Primary and Standby database should use the same recovery catalog. Even though these database share the same DBID,Rman is able to differentiate the standby database from Primary .
Note you do not need to register the standby database in the catalog if the primary is already registered. Simply connect to the standby as target and then connect to recovery catalog for taking backup.
RMAN> backup database plus archivelog ;
RMAN> backup current controlfile;
Note: In 10g, you will need to backup the controlfile from the primary site.
The above will result in a consistent, self-contained backup.
3) restart managed recovery:
To restore from this backup:
RMAN> startup nomount;
RMAN> restore controlfile from 'controlfile backuppiece name and location';
RMAN> alter database mount;
RMAN> restore database;
RMAN> recover database noredo;
RMAN> restore controlfile from 'controlfile backuppiece name and location';
RMAN> alter database mount;
RMAN> restore database;
RMAN> recover database noredo;
Sunday, November 24, 2019
Creating an SSH Key Pair on the Command Line
To create an SSH key pair on the command line using
ssh-keygen:- Open a shell for entering the commands.
- At the prompt, enter the following:
ssh-keygen -t rsa -N "" -b "2048" -C "key comment" -f path/root_namewhere the arguments are as follows:-t rsaUse the RSA algorithm. -N "passphrase"Passphrase to protect the use of the key (like a password). If you don't want to set a passphrase, don't enter anything between the quotes.Note: While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use.-b "2048"Generate a 2048 bit key. You don't have to set this if 2048 is acceptable, as 2048 is the default.Note: A minimum of 2048 bits is recommended for SSH-2 RSA.-C "key comment"A name to identify the key. -f path/root_nameThe location where the key pair will be saved and the root name for the files. For example, if you give the root name asid_rsa, the name of the private key will beid_rsaand the public key will beid_rsa.pub.For example,
Alternatively, you can simply enter ssh-keygenand then enter responses when prompted for a name and a passphrase. The keys will be created with default values: RSA keys of 2048 bits. 
To see that the files were created, type ls path/root_name*, for example,
Creating SSH Keys for Use with Oracle Cloud Services
To generate an SSH key pair using the PuTTY Key Generator,
- Find
puttygen.exein the PuTTY folder on your computer, for example,C:\Program Files (x86)\PuTTY. Double-clickputtygen.exeto open it.
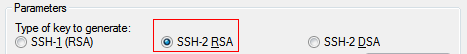
- Accept the default key type, SSH-2 RSA.SSH-2 is the most recent version of the SSH protocol (and is incompatible with SSH-1). RSA and DSA are algorithms for computing digital signatures.
- Set the Number of bits in a generated key to
2048bits, if it is not already set with that value.This sets the size of your key and thus the security level. A minimum of 2048 bits is recommended for SSH-2 RSA.
- Click Generate.
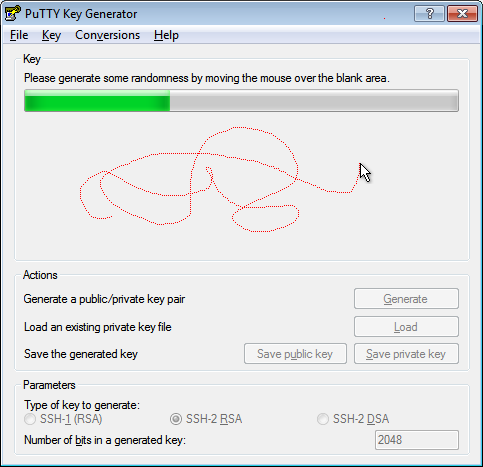
- Move your mouse around the blank area to generate randomness to the key.Note: the dotted red line in the image below is for illustration purposes only. It does not appear in the generator pane as you move the mouse.
- The generated key appears under Public key for pasting into OpenSSH authorized_keys file.
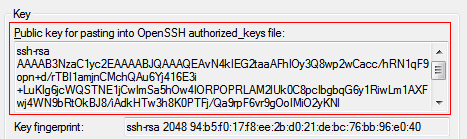
- The key comment is the name of the key that you will use to identify it. You can keep the generated key comment or create your own.

- If you want to password-protect your key, enter a Key passphrase and enter it again for Confirm passphrase. When you reload a saved private key, you will be asked for the passphrase, if one is set.
 While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use.There is no way to recover a passphrase if you forget it.
While a passphrase is not required, you should specify one as a security measure to protect the private key from unauthorized use.There is no way to recover a passphrase if you forget it. - Save the private key of the key pair. Depending how you work with the private key in the future, you may need one saved in the PuTTY PPK format and one saved in OpenSSH format. Let's do both.
- To save the key in the PuTTY PPK format, click Save private key to save the private key of the key pair.
 You can name it anything you want, although you may want to use the same name as you used for the key comment. The private key is saved in PuTTY's Private Key (PPK) format, which is a proprietary format that works only with the PuTTY toolset.
You can name it anything you want, although you may want to use the same name as you used for the key comment. The private key is saved in PuTTY's Private Key (PPK) format, which is a proprietary format that works only with the PuTTY toolset. You can use this key whenever you use Putty to perform SSH actions.
You can use this key whenever you use Putty to perform SSH actions. - To save the key in OpenSSH format, open the Conversions menu and select Export SSH key. This will be the same key as above, just saved in a different format.
 You can name it anything you want, but to keep track of your keys, you should give it the same name as the key you saved in PPK format in the previous step. You can also use any extension (or no extension), but let's use
You can name it anything you want, but to keep track of your keys, you should give it the same name as the key you saved in PPK format in the previous step. You can also use any extension (or no extension), but let's use.ssh, to make it clear what format it is. You can use this key whenever you use OpenSSH to perform SSH actions using ssh utitlities that support OpenSSH, for example when using Linux in a command shell.
You can use this key whenever you use OpenSSH to perform SSH actions using ssh utitlities that support OpenSSH, for example when using Linux in a command shell.
- Now you need to create the public key to be paired with the private key(s) you just created. However, clicking the Save public key button will create a public key that won't work with Oracle Cloud services in certain cases. So, for the purposes of this tutorial, there is no reason to save a public key using the Save public key button.
 Instead, proceed as follows.
Instead, proceed as follows. - In the PuTTY Key Generator, select all of the characters under Public key for pasting into OpenSSH authorized_keys file.Make sure you select all the characters, not just the ones you can see in the narrow window. If a scroll bar is next to the characters, you aren't seeing all the characters.

- Right click somewhere in the selected text and select Copy from the menu.

- Open a text editor and paste the characters, just as you copied them. Start at the first character in the text editor, and do not insert any line breaks.

- Save the key as a text file, using the same root name as you used for the private key. Add a
.pubextension. You can give it any extension you want, but.pubis a useful convention to indicate that this is a public key.
- Write down the names of your public and private keys, and note where they are saved. You will need the public key when creating service instances in, for example, Oracle Java Cloud Service and Oracle Database Cloud - Database as a Service. You will need the private key when trying to access a service instance's virtual machine via SSH.
Thursday, July 4, 2019
Using Office 365 in Workflow Notification mailer in Test environments Configuration steps
Using Office 365 in Workflow Notification mailer in Test environments
Steps1- Configure the mail server and email sender
1. Login using ‘SYSADMIN user and go to responsibility 'System Administration' > Oracle Applications Manager > Click on Workflow
2. Screen displayed as Notification mailer Down
3. Click on 'Service Components'
4. Select Workflow Notification Mailer and click on Edit.
Set the following parameters
a) Outbound EMail Account (SMTP)
Server Name: 'smtp.office365.com'
Username: 'mailer@Company.com'
Password: 'password'
Connection Security: 'STARTTLS'
b) Inbound EMail Account (IMAP)
Server Name: 'outlook.office365.com'
Username:'mailer@Company.com'
Password:'password'
Reply-To Address: 'mailer@Company.com'
Connection Security:'SSL/TLS'
5. Click on button 'Advanced'
6. Press 'Next'
7. Press 'Next'
8. Press 'Next'
9. Update from field to ‘Workflow Mailer Test Environment’ and click on finish.
10. Click on finish
Steps2 - Configure the override address
Override email address is very imported in test environment. all the emails will be redirected to this email. Following are the steps to set it up from back end.
Override email address is very imported in test environment. all the emails will be redirected to this email. Following are the steps to set it up from back end.
1. Run the below sql statement
SELECT fscv.parameter_value
FROM fnd_svc_comp_params_tl fscp, fnd_svc_comp_param_vals fscv
WHERE fscp.display_name = 'Test Address'
AND fscp.parameter_id = fscv.parameter_id;
Query will result with value ‘NONE’ if override is not set earlier.
Query will result with value ‘NONE’ if override is not set earlier.
2. Now run the below sql update statement and commit
UPDATE fnd_svc_comp_param_vals fscpv
SET fscpv.PARAMETER_VALUE = 'erp.test02@company.com' --(Email address to which all emails will be redirected)
WHERE fscpv.parameter_id IN (SELECT fscp.parameter_id
FROM fnd_svc_comp_params_tl fscp
WHERE fscp.display_name = 'Test Address');
3. Now run the below SQL again to verify that the override email address has been set as required.
SELECT fscv.parameter_value
FROM fnd_svc_comp_params_tl fscp, fnd_svc_comp_param_vals fscv
WHERE fscp.display_name = 'Test Address'
AND fscp.parameter_id = fscv.parameter_id;
Query will result with value 'erp.test02@company.com'.
4. Start the workflow mailer from 'System Administration' > Oracle Applications Manager > Click on Workflow
Select Workflow Notification mailer and Click on Select ‘Start’ from drop down list and Press on Go button.
5. Workflow notification mailer should start and the status should be 'Running'.
Steps3 - Test the setup
1. Click on 'Workflow Notification Mailer'.
2. Click on ‘Test Mailer’
3. Select user with email address set and click 'Accept' button.
Email address which has been set to override will receive two email.
The emails should not be sent to the actual email address that is set for the user which selected above.
Now test environment has been configured to test workflow mailer server.
Subscribe to:
Comments (Atom)
Enable YUM in OCI DBaaS Compute Instances
If you have some DBaaS computes nodes in your OCI, you will note that they don't come with any YUM repo configured by default. This is...
-
To create an SSH key pair on the command line using ssh-keygen : Open a shell for entering the commands. At the prompt, enter the followin...
-
If you have some DBaaS computes nodes in your OCI, you will note that they don't come with any YUM repo configured by default. This is...
-
Loading…












